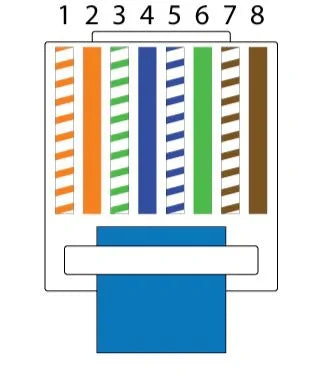
Tail Cable Repair Guide for Techage POE Camera
2 Comments
Best Security Camera App for iPhone
0 Comments
How to Keep Spider Webs off Security Cameras?
0 Comments
Can Battery-Powered Cameras Really Support 24/7 Recording?
0 Comments
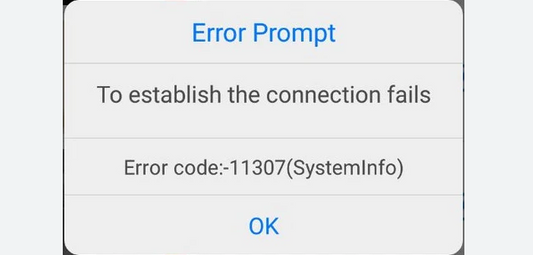
Comprehensive Guide to Common Error Codes in Security Camera Apps: Reolink, Ring, and Eufy
1 comment